Introduction
In this tutorial, we will learn about how to install Metasploitable 2 on VirtualBox using 5 simple steps. Metasploitable 2 is intentionally insecure and is not intended for use in production environments. Metasploitable 2 exclusively used for educational and testing purposes. Let is understand basic of Metasploitable 2 along with security risk involved which must be checked before installing it.
Metasploitable 2 Overview
Metasploitable 2 is a deliberately vulnerable virtual machine(VM) designed for security testing, penetration testing and ethical hacking purposes. It is a platform that provides a safe and controlled environment for security professionals, ethical hackers and students to practice and develop their skills in identifying and exploiting vulnerabilities commonly found in various operating systems and applications.
![How to Install Metasploitable 2 on VirtualBox: [5 Simple Steps]](https://www.linuxnasa.com/wp-content/uploads/2023/09/metasploitable.jpg)
Security Precautions
- Metasploitable 2 must be used in controlled and isolated environments such as, virtualized environments like VirtualBox, VMware or other hypervisors.
- Users should have proper authorization and consent before conducting security assessments using Metasploitable 2.
- Responsible and ethical use of Metasploitable 2 is essential as some of the vulnerabilities in the VM can be unstable or crash the system.
How to Install Metasploitable 2 on VirtualBox: [5 Simple Steps]
Also read: How to Install Kali Linux 2023.3 on VirtualBox: [7 Simple Steps]
Prerequisite
- VirtualBox Installed
- 1GB free disk space
Step-1: Download Metasploitable 2 Archive
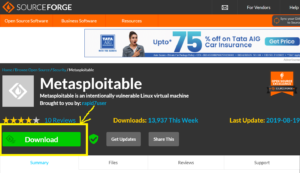
In this step, we will download the Metasploitable 2 archive. To do so, open sourceforge.net and click on Download button as shown below.
Step-2: Untar Metasploitable 2 Archive
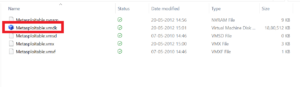
In this step, untar the Metasploitable arhive file. After untaring, you will find few files including the .vmdk file which we will use to install the Metasploitable in Virtual machine.
Step-3: Create new Virtual Machine
In this step, open VirtualBox and click on ‘new‘ button to create a new virtual machine as shown below.
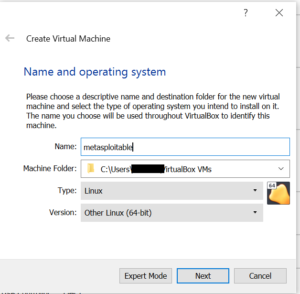
Next, assign a name to the virtual machine. I have given the name ‘metasploitable’. Select Linux as Type from the drop down. Select Other Linux (64-bit) as Version from the drop down as shown below. Once all done, click on Next.
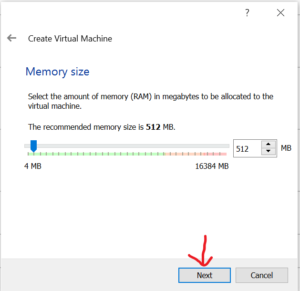
Next, select the memory size. 512MB size should be enough. Once done click on Next as shown below.
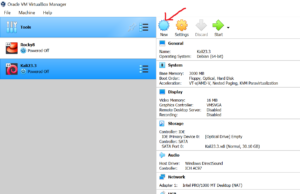
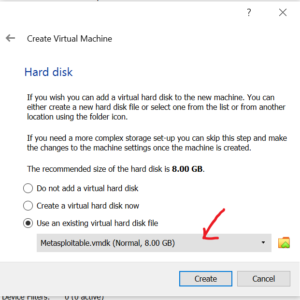
Next, select ‘Use an existing virtual hard disk file‘ since we have .vmdk file . Click on choose icon to provide the Metasploitable .vmdk file path as shown below. After selecting the .vmdk file, click on Create button to create the virtual machine.
Step-4: Install Metasploitable 2
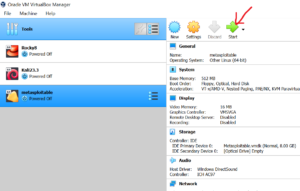
In this step, click on Start button to start installing the Metaspoitable 2 as shown below.
Next, wait for few seconds until it start the machine. Once done, you will see a login pop up as shown below.
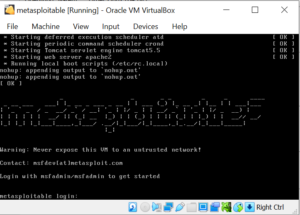
Step-5: Login to Metasploitable 2 Machine
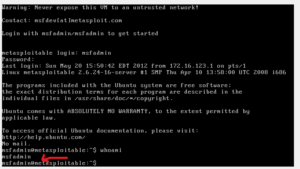
In this step, we will login to Metasploitable 2 machine. The default credential to login into the machine is msfadmin/msfadmin. Try to login into the machine using this credential as shown below. Once you get into the machine, you can check which user is connect by executing the command ‘whoami’.
Summary
Metasploitable 2 is a valuable tool for security professionals and students to gain hands-on experience with security vulnerabilties and penetration testing techniques.